The 8 Stages of a Pig Butchering Scam
The common steps pig-butchering scammers follow to lure victims and extract their assets.
Table of Contents
The 8 Stages of a Pig Butchering Scam
Before you can respond effectively to a pig‑butchering scam, it helps to understand exactly how the scam unfolds from the very first contact. One of the aspects that makes pig-butchering so effective is the depth of the relationship the victim builds with the scammer.
This technique means victims may remain in denial long after the scammers have halted communications or blocked platform withdrawals. Recognizing the patterns that exist across all pig-butchering scams can help victims move towards healing and the possibility of asset recovery.
This section breaks down the lifecycle of the scam we see in our practice over and over again into discrete phases. If you see your own experience in any of these steps, treat it as a cue to stop, document everything, and get advice from an attorney or certified investigator before sending another dollar.
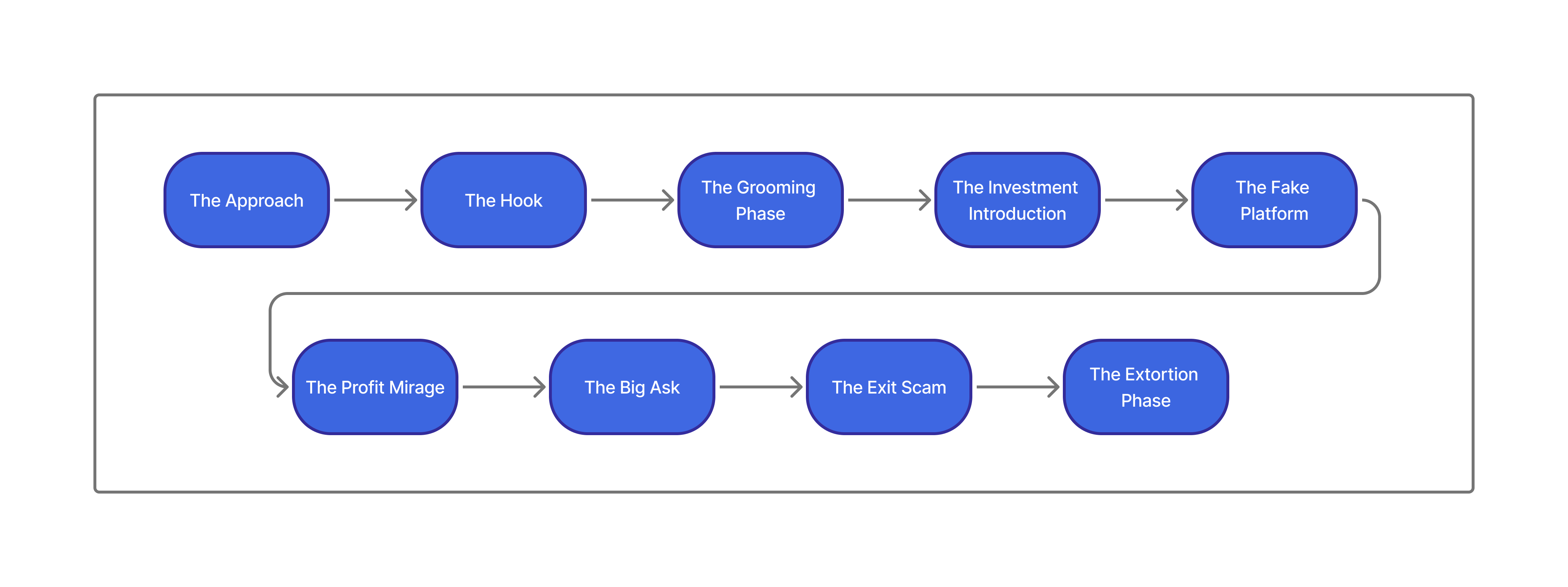
Stage 1: The Approach
The scam almost always begins with with something that feels mundane and low‑stakes: a wrong‑number text, a random social‑media follow, or a surprisingly polished dating‑app match.
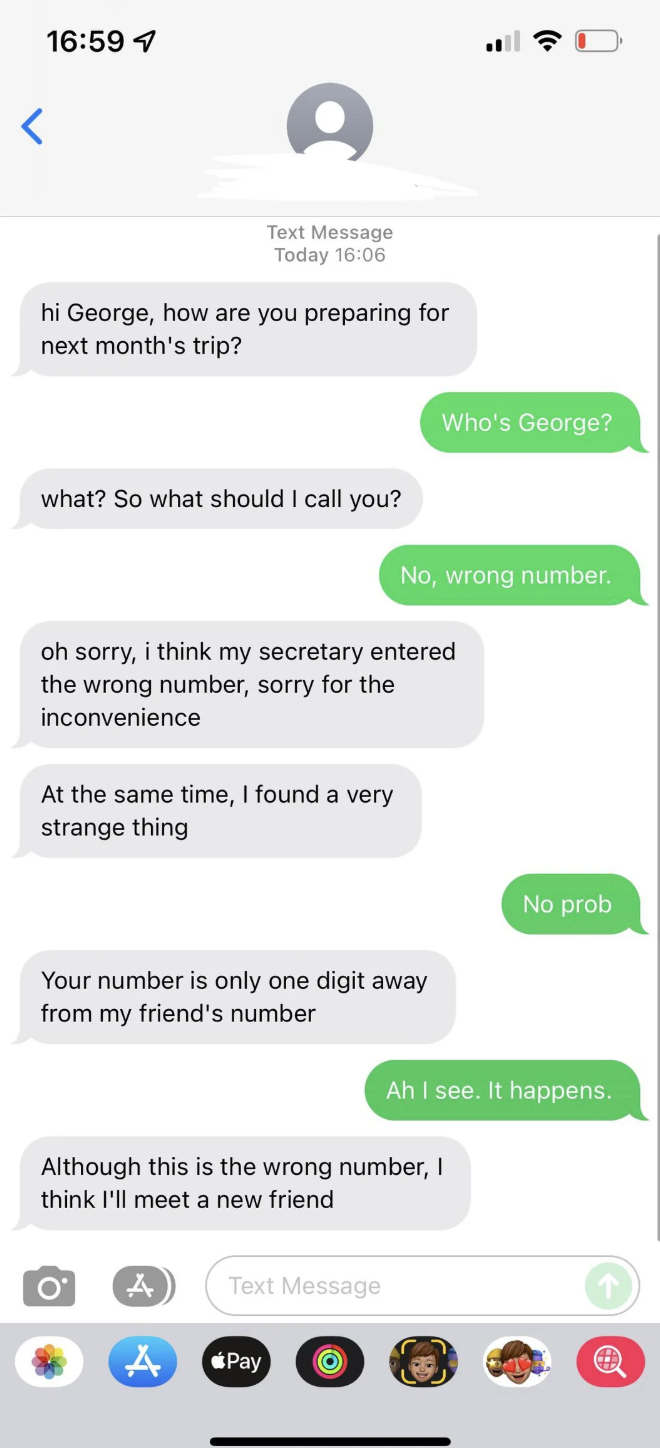
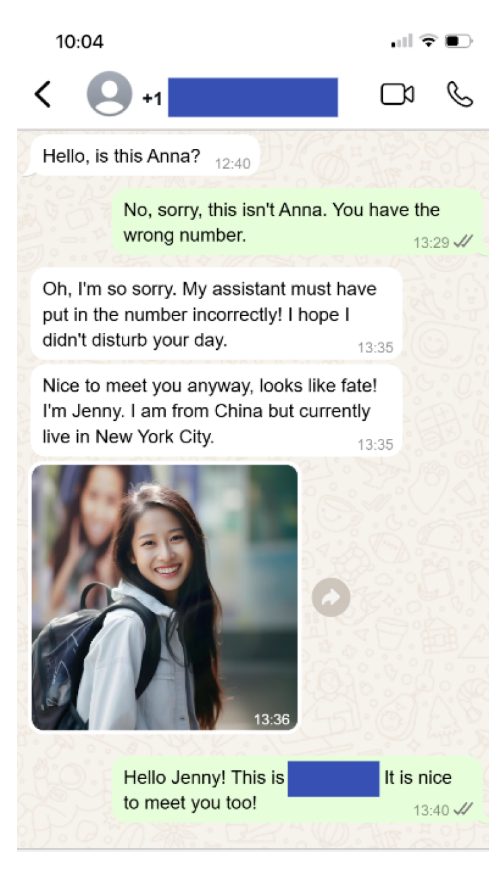
Wrong‑Number Texts
One of the most common entry points we see is a simple, casual text to your mobile number:
- “Hi Anna, are we still on for dinner?”
- “Did you receive the documents I sent yesterday?”
- “Hello Mr. Chen, this is Lisa from the investment group.”
When you reply "Wrong number," the scammer doesn't just apologize and disappear. Instead, they pivot instantly into friendly small talk, often with an unusual level of warmth for a stranger:
“Accidental Message” Scripts
Closely related to wrong‑number texts are “accidental” messages sent via WhatsApp, Telegram, or other encrypted apps:
- A photo of a meal with “Table is ready”
- A screenshot of supposed trading profits
- A voice note clearly intended for someone else
When you respond that they have the wrong person, the script is nearly identical: profuse apologies, light humor, then a quick attempt to keep the conversation going.
What looks like spontaneity is usually a tested, copy‑and‑paste script used across dozens or hundreds of victims.
LinkedIn Professional Lures
Scammers may also masquerade as new professional connections through platforms like Linked-In. Red flag messages include:
reference link: https://www.wsj.com/arts-culture/books/online-scammer-steals-live-savings-6a510f6d
- A random connection request from someone claiming to be a “senior analyst,” “wealth manager,” or “blockchain consultant.”
- Messages praising your background, then asking to “compare notes” on markets or “share investment insights.”
The tone here is collegial and businesslike, not flirtatious.
Scammers lean on fake titles, fabricated company names, and jargon‑heavy messages to position themselves as credible financial insiders. Watch out for profiles with very recent creation dates but hundreds of connections, work histories that don’t match public records or known firms, and stock‑image profile photos or AI‑generated headshots.
Tinder / Bumble Romance Approaches
On dating apps, the approach is carefully engineered to feel like a dream match, not a cold outreach:
- Profiles often show travel, fitness, luxury dining, and subtle hints of wealth.
- Bio lines frequently reference “financial freedom,” “crypto trading,” or “helping friends invest wisely.”
- Early messages escalate quickly into long, emotionally intimate chats.
Instead of pushing for an in‑person meeting right away, scammers often prefer to move you off‑platform—to WhatsApp, Telegram, or SMS—where moderation and reporting tools are weaker.
From there, they gradually steer the conversation toward trading, “side hustles,” and “opportunities” you could pursue together.
How to respond at this stage
Preserve these early interactions.
They often establish:
- The origin platform (phone carrier, WhatsApp, Telegram, Instagram, Tinder, Bumble, LinkedIn, etc.).
- The initial phone number, handle, or profile URL that may later be tied to other victims.
- Early clues that the scammer is following a script rather than behaving like a genuine acquaintance.
Screenshots, profile links and message metadata can later help a cybercrime lawyer or investigator connect your case to a wider scam network.
As you'll see in the next phase—the Hook—the scammer's goal during the Approach is simple: Convert a stranger into a trusting, emotionally invested contact who will be receptive when the "investment opportunity" finally appears.
Stage 2: The Hook
Once the scammer has your attention, they shift to turning casual contact into real attachment. On the surface, this looks like a new friend or romantic partner taking genuine interest. In reality, scammers are following a script designed to build trust and dependence that opens the door to poor financial decision making.
Rapport‑Building Scripts
Scammers use repeatable scripts that feel personal but are deployed across hundreds of victims. They ask about your family, work, and goals, then mirror your answers back to create false intimacy.
Red flags include:
- Fast escalation: Early use of nicknames, endearments, and talk of "fate" or "destiny."
- Mirrored struggles: Stories about their own losses that conveniently echo yours .
- Future‑oriented talk: References to retiring together, shared property, or joint business plans.
Reference link: https://www.reddit.com/r/Scams/comments/njimju/pigbutchering_scam_sha_zhu_pan_photos_of_training/
Scanners may also send voice notes, selfies, gym photos, and workspace shots to make the relationship feel real. They establish daily check‑in routines, share curated images of wealth and success, and create reciprocity pressure by nudging you to share more of your own life.
Tip
Preserve these assets: Screenshots with profile names, timestamps, and media can help forensic teams determine whether images are stolen or reused across multiple scam profiles.
Fake Credentials and Business Personas
As rapport solidifies, scammers introduce a formal persona: successful entrepreneur, crypto trader, or finance professional with "rare access" to profitable opportunities. The emotional bond makes these claims feel believable.
Common tactics include:
- Screenshots of trading dashboards showing consistent profits.
- Photos of conference badges, office buildings, or business cards with impressive titles.
- Stories about "helping friends and family" achieve financial freedom.
The sum of these parts is often a pre‑packaged character with fake company names, unverifiable titles, and recycled images across multiple identities.
Fake platform.png
As the Hook phase progresses, conversations drift from "How was your day?" to "Here's how I invest"—the bridge into the Grooming Phase where emotional dependence and financial advice become intertwined.
Stage 3: The Grooming Phase
In the Grooming Phase, the scammer shifts from building connection to shaping your habits, routines, and decision‑making around them.
By this point, many victims describe feeling as if this person is part of their daily life—a source of encouragement, advice, and emotional support.
Legal perspective
Grooming demonstrates how the scammer systematically engineered trust and influence before any major investment was discussed.
That pattern can help distinguish legitimate financial advice from a premeditated crypto scam or pig‑butchering operation.
In practice, grooming usually shows up as a handful of repeatable patterns:
Rhythm and routine. Good‑morning and good‑night messages, midday check‑ins, and constant small talk that normalize continuous contact. Over time, chat logs show dense streams of messages with very few gaps.
Emotional mirroring. When you share stress about work, health, or family, the scammer responds with empathy, “similar” stories, and promises that financial security will fix many of your problems. They often repeat your own phrases back to you and claim to have gone through “the same thing.”
Shared “our future” language. Conversations shift from your goals to “our” goals—retiring together, buying property, traveling once “our portfolio” hits a target number. Screenshots of their supposed investments are framed as what “we can get you to” if you are “brave enough” to follow their plan.
Taken together, these tactics blur the line between personal loyalty and financial judgment.
By the time the investment pitch appears, many victims feel they would be letting down someone they care about—not just turning down a risky trade.
Stage 4: The Investment Introduction
Once the emotional groundwork is laid, the scam finally begins to look like an “investment opportunity.”
Transition from Personal to Financial
The shift into money talk is rarely abrupt.
Instead, it often starts with casual references to how the scammer manages “their” finances or how they achieved their current lifestyle.
Common openings include:
- Comments about making “extra income” from crypto or foreign‑exchange trading.
- Screenshots of account balances or profit charts shared “just to motivate you.”
- Stories of helping a sibling, friend, or colleague pay off debts or retire early through the same approach.
Crucially, the scammer frames this as sharing something special with you, not selling a product. They emphasize exclusivity, timing, and the idea that you are being invited into a more sophisticated level of investing.
Claims of Crypto Expertise
To make the invitation credible, scammers may describe themselves as early crypto adopters, quantitative traders, or insiders with professional experience at major financial institutions. They may share:
- Screenshots of detailed trading interfaces with complex charts and indicators.
- References to specific coins, pairs, or strategies that sound technical and impressive.
- Explanations that they have “a system” or “mentor” that consistently beats the market.
Victims often report feeling out of their depth at this stage, but reassured by the prior emotional bonding. From an evidentiary standpoint, these chats can show how the scammer knowingly presented themselves as an expert to induce reliance on their advice.
Pressure via Urgency and Authority
As the investment angle becomes clearer, the tone often shifts from purely supportive to gently insistent.
The scammer highlights limited‑time opportunities, market windows, or “entry points” that supposedly require quick action.
Typical language includes:
- “If you wait too long, you’ll miss this cycle.”
- “I only share this with a few people I trust.”
- “I don’t want you to regret not starting when you had the chance.”
This often marks the point where many victims first move money from traditional accounts into cryptocurrency exchanges.
Stage 5: The Fake Platform and Profit Mirage
Once you’ve agreed in principle to “invest,” the scammer introduces a platform, app, or website where the trading supposedly happens. This infrastructure is central to pig‑butchering scams: it’s where your deposits are displayed, your “profits” are fabricated, and your withdrawals are ultimately blocked.
These setups tend to follow a recognizable pattern:
- Convincing wrappers: Websites, mobile apps, Web3 dApps, and mirror sites mimic real brokers and exchanges—complete with charts, order books, KYC flows, and support chats. Domains may differ from real brands by only a character or two, and “customer support” is staffed by the same scam operation.
- Scammer‑controlled deposit funnels: You are given deposit addresses or QR codes, or asked to connect a wallet and approve transactions. On‑chain, those addresses almost always resolve to wallets directly controlled by scammers, not regulated institutions.
- Fabricated performance: Once funds arrive, the dashboard shows near‑instant crediting and smooth, often unrealistic growth. Balances and profit figures are entirely under scammer control; there are no real trades behind the numbers.
- UX that pushes deposits, not withdrawals: Buttons to “add funds” or “increase position size” are prominent, while withdrawals are buried, delayed, or subject to sudden “maintenance” and “compliance checks.” Regular prompts about limited‑time opportunities, badges tied to deposit size, and celebratory messages from your scammer‑contact all push you to keep topping up.
The combination of look‑alike infrastructure, scam‑controlled wallets, and unverifiable trading activity is one of the strongest signals that a pig‑butchering platform is in play—even before the final cut‑off.
Stage 6: The Big Ask
At some point, the scam shifts from incremental deposits to a single, much larger commitment.
This is often the moment when victims move retirement funds, home‑equity proceeds, or the bulk of their savings.
“One Big Deposit” Scripts
Scammers frequently frame this request as a special chance to level up.
They may claim that a particular trade, coin, or market window is uniquely favorable and that you should “seize the moment.”
Common lines include:
- “If you can make one bigger deposit now, you won’t have to worry about money again.”
- “This is the last chance before the next halving / cycle / window closes.”
- “You trust me, right? I wouldn’t suggest this if I wasn’t sure.”
These messages often come after weeks or months of apparent success on the fake platform, making the leap feel less risky than it truly is.
Social‑Engineering Nudges
To overcome hesitation, scammers deploy every tool of social engineering they’ve developed during earlier phases They may combine flattery, mild disappointment, urgency, and even implied threats about missed opportunities.
These tactics are designed to override your internal risk alarms precisely when the stakes are highest.
Stage 7: The Exit Scam
After the Big Ask, many victims notice a subtle but decisive change.
Suddenly, withdrawals stop working, support becomes evasive, and the person who once messaged you begins to disappear.
Sudden Disappearance and Delays
The first signs of the exit often look like ordinary technical issues:
- “System maintenance” messages when you try to withdraw.
- Requests to wait a few hours or days for “liquidity” or “compliance checks.”
- Customer‑support tickets that receive vague or copy‑and‑paste responses.
On the chat side, the scammer may:
- Respond more slowly or at odd hours.
- Blame the platform, regulators, or “the finance team” for delays.
- Reassure you that everything is fine as long as you don’t panic.
“Customer Service” as a Wall
As problems escalate, you are often pushed toward platform “customer service” instead of your original contact.
This creates a buffer that lets the scammer maintain emotional rapport while the platform continues to stonewall.
You may experience:
- Being asked to submit identity documents or additional information under the guise of compliance.
- Being shuffled between multiple support reps who all give the same scripted answers.
- Feeling that you’re trapped in a loop without any clear path to resolution.
These delays buy time for scammers to move funds further down the chain, making recovery harder.
Stage 8: The Extortion Phase
For many victims, the scam does not end when withdrawals fail.
Instead, it evolves into a final phase of extortion and secondary scams that aim to extract even more money.
Fake Taxes and Unlocking Fees
One common tactic is to claim that your funds are “frozen” until you pay additional charges:
- Supposed tax obligations to a foreign regulator.
- “Security deposits” or “risk reserves” that must be posted before release.
- High “service fees” or “gas fees” that must be prepaid.
These demands are almost always time‑sensitive and accompanied by official‑looking invoices or documents.
Paying them rarely, if ever, results in access to your funds.
Threats, Time Pressure, and Recovery Scams
In more aggressive cases, scammers escalate to threats and follow‑on schemes:
- Implying legal trouble if you do not pay alleged taxes or fees.
- Threatening to report you to authorities for “money laundering” or “tax evasion.”
- Introducing a new “lawyer,” “recovery agent,” or “compliance officer” who claims they can fix everything—for an upfront payment.
This is where many victims lose a second round of funds, desperately trying to unlock what is already gone.
Important
Real crypto recovery lawyers offer free in-person consultations and will not ask for payment upfront. Be sure to meet and interview your attorney before making any payments. For a list of good questions to ask a crypto recovery lawyer, see our checklist.

